Cyber Security Management
To improve the cyber security governance and defense capabilities, the Company has established an internal control system. All information operations are subject to the internal control system and the risk management review by the internal and external units on a regular and daily basis.
[Cyber Security Governance System, Goals and Strategies]
To enhance its cyber security management, Weltrend adopts an effective cyber security defense network as its vision, focusing on a consistent cyber security governance system. The Information Security Department oversees the establishment and compliance of the security system, driving the implementation of relevant practices while continuously improving security awareness and expertise. By leveraging technology, security risks and vulnerabilities are identified and strengthened, building a comprehensive governance system and all-around protection capability, while fostering a strong awareness of cyber security among employees.
[Implementation of Cyber Security Policy]
- Establish cyber security management regulations that comply with legal and customer requirements.
- Promote organization-wide awareness to achieve consensus on comprehensive security protection.
- Safeguard the confidentiality, integrity, and availability of company and client information to ensure business continuity.
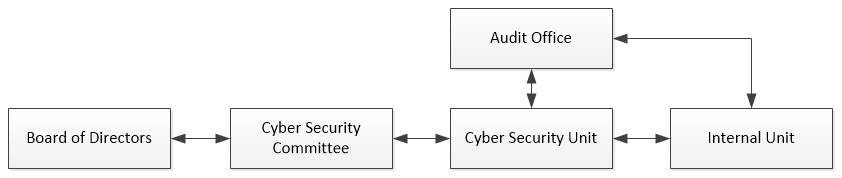
[Information Security Structure]
- Information Security Management Committee: Led by the company's President and comprised of unit managers (or their deputies), this committee is responsible for decisions regarding the information security management system, reviewing security policies, and designing the management structure and functions. It also examines and reviews the development, implementation, and execution of the Company's overall information security management system, and regularly reports on the status of information security governance to the chairman and the board.
- The Management Information Department is responsible for cyber security risk management, executing security policies, training personnel, implementing and auditing security measures, and improving internal procedures based on audit results.
- The Audit Office oversees cyber security supervision, ensuring internal security is properly executed. If any deficiencies are found during audits, the relevant unit is required to submit improvement plans and specific actions, with progress monitored to reduce internal security risks.
[Cyber Security Management Plan]
The Company has established a Cyber security management plan for all employees to follow:
- Develop a management plan covering email control, firewall setup, antivirus software, system program access control, and internet intrusion protection. Regularly check the System Log of each network service item to track the abnormal situation
- Assign different access levels based on employee roles, continuously promoting security information to increase awareness. intrusion protection. Regularly check the System Log of each network service item to track the abnormal situation.
- Regularly exercise the system for restoration every year and review emergency response plans.
- Perform annual internal audits, accountant reviews, and ISO audits to strengthen security management.
- Join TWISAC/SPISAC/TWCERT to receive and share critical threat intelligence and stay updated on current trends.
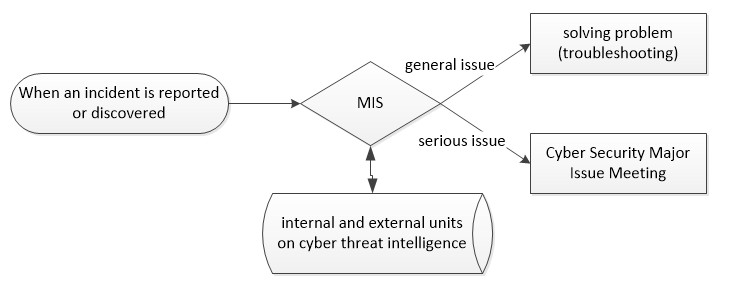
[Information Security Incidents]
The Company has established clear procedures for reporting and handling information security incidents. When an incident is reported or discovered, the information department logs it, classifies its severity, and resolves it within the targeted timeframe. After resolving the incident, a root cause analysis is conducted, and corrective measures are implemented to prevent recurrence.
[Resources Invested in Cyber Security Management]
Implementation status in 2024
- Continue to invest resources in information security-related fields. Resource investment includes improving governance and technical infrastructure, strengthening information security defense equipment, endpoint monitoring threat systems, intelligence monitoring and analysis, information security incident response drills and education training, etc. Related matters
- In order to deepen information security and confidential information protection, we will continue to strengthen management systems and technologies. This year, we will add vulnerability scanning to review the security status of the company's network and systems to enhance information security capabilities and protect the company's important information assets.
- The company has set up an information security management committee and a dedicated information security staff. The committee has 10 members. Among the dedicated information security staff, there is one information security officer and two information security personnel.
- In terms of information security risk management, conduct an annual inventory of information security assets, and set execution priorities based on the size of the risk impact and improvement costs.
- Accepted 2 annual audits by external risk management agencies this year.
- In terms of information security promotion, we regularly conduct information security promotion and send related promotions to colleagues 4 times every quarter. We also send 19 emails to promote information from time to time in response to information. The content includes reminding colleagues to pay attention to phishing letters, pay attention Issues related to the importance of backup data and passwords.
- In response to the revision of the "Information Security Management and Control Guidelines for Listed Over-the-Counter Companies", in addition to revising the order of provisions, sections 23, 24, 25, and 34 have been revised, and the company's information security operating standards have also been revised, sections 5.3.6 and 5.5. 3 points.
- The dedicated information security unit receives 3 times of information security education and training, holds an Information Security Management Committee meeting once a year, and conducts an information security governance implementation report at the meeting. Relevant information is also submitted to the board of directors for reporting.
- There were no incidents that endangered the company’s information security in 2024.